Italian privacy dawn raids are a hot topic and being prepared to them is crucial, especially given the potential fines provided by the GDPR. Here are the main takeaways from our event on the matter.
On the 1st of March 2019, DLA Piper had the pleasure to host – together with AIGI – an event on Italian privacy dawn raids that had as main speaker, Mr. Marco Menegazzo, the head of the department of the tax police in charge of privacy dawn raids, supporting the Italian data protection authority (the Garante) on their performance.
Other speakers included Cristina Cabella, Chief Privacy Officer at IBM, Sandra Mori, Data Privacy Officer Europe at Coca-Cola, and Laura Botticini, Head of Legal Support on Labour, Safety and Privacy at A2A that gave their perspective on the most relevant issues to be dealt during privacy dawn raids and in general in the performance of their activity in large corporations.
Below are our main takeaways from the discussion:
1. False information in privacy documents can lead to criminal liabilities
Mr. Menegazzo emphasized that during Italian privacy dawn raids companies sometimes provide a record of processing activities that does not actually reflect their data processing activities. Likewise, privacy information notices and the internal privacy compliance organization of companies are often mere formalities,
- either quickly arranged in the urgency of showing some sort of GDPR compliance that can be easily challenged during an investigation,
- or adopted in line with the one received by the group for consistency and because it is excessively burdensome to differentiate it on the basis of the peculiarities of each subsidiary.
This is especially true in Italy since there is no legal privilage on privacy investigations and therefore officers of the tax police and the Garante can perform a back-up of emails, get access to IT systems and interview the personnel of the company.
But the matter is even more relevant since, according to Mr. Mengazzo, the Italian Privacy Code provides the criminal sanction of the imprisonment between 6 months and 3 years for “false statements to the data protection authority“that in his view could be triggered by a record of processing activities and other documents provided to the tax police and the data protection authority during a dawn raid that do not represent the actual data processing activities performed by the company.
ACTION NEEDED: Make sure that the record of processing activities and the privacy information notices reflect the actual data processing activities and are not just documents either received for instance from the group or difficult to understand. This will require to run interviews with the relevant personnel and to have in place adequate an adequate privacy compliance organization structure so that in case of new data processing activities, the documents are updated.
2. You need to be ready for an Italian privacy dawn raid
Dawn raids occur by definition with no prior notice. The tax police comes to your office and requests to provide the requested documentation and information. According to Mr. Menegazzo, this request starts analizing:
- The record of processing activities;
- The data protection impact assessments that have been performed; and
- The letter of appointment of the DPO.
These documents shall be ready, up to date and reflect the actual data processing activities performed by the company. Indeed, Mr. Menegazzo made clear that, in the light of the principle of accountability, they expect companies to be able to prove any of their decisions on privacy compliance and activities on the processing of personal data.
But it was also interesting the feedback on the topic from our panelists. Privacy dawn raids normally last 4-5 consecutive very long days in which there is a deep scrutiny of the company, of its IT systems and personnel. If there is no internal procedure on how to handle privacy dawn raids and a dedicated training to the personnel on their performance, there is a risk that inaccurate information is provided to the authority.
In particular, Sandra Mori from Coca-Cola emphasized that they found very useful to perform privacy dawn raids mockups, simulating an investigation from privacy authorities, Cristina Cabella from IBM stressed that the amount of work and effort that they put in training their personnel and creating awareness around privacy compliance is massive and Laura Botticini from A2A declared that the internal organization is crucial in properly handling a dawn raid.
ACTION NEEDED: Draft a policy on the performance of privacy dawn raids and have privacy related documents ready to be provided to authorities in case of inspections. Also, perform a training on the policy with your personnel and even a mockup of a dawn raid. The misbehaviour of personnel during a dawn raid is one of the major risks to be faced.
3. DPOs have to be real and present
Mr. Menegazzo criticized the decision taken by some companies to appoint a DPO that
- cannot be easily reached and stressed that he wants the DPO to be present during the dawn raid;
- is not able to prove to run an actual control on the processing of personal data performed by the company and requested to provide evidence of the minutes of meetings with DPO and of the activities performed by DPOs, especially in the case of external DPOs or when a single DPO acts for large multinational corporations without being able to speak the local language;
- have not been formally appointed and remarked the need to provide the copy of the letter of appointment and of the internal reporting performed by the privacy champions to the DPO.
He continously repeated that during an investigation they try to understand what is beyond mere formal documents, digging into the actual data processing activities performed by the company and the measures that the company is able to prove to have adopted to ensure privacy compliance.
ACTION NEEDED: Identify a DPO that is actually easily accessible, involved in the business and can reach the office of the company in less than a day. Also, make sure that the DPO is formally appointed by means of a letter of appointment and a board resolution, if a director of the company does not have the powers to appoint him/her. The same applies for the appointment of privacy champions, persons in charge of data processing and any individual that is part of the company’s privacy compliance organization structure. Additionally, every meeting with the DPO and any decision taken by the company, including the decision not to appoint a DPO shall be documented.
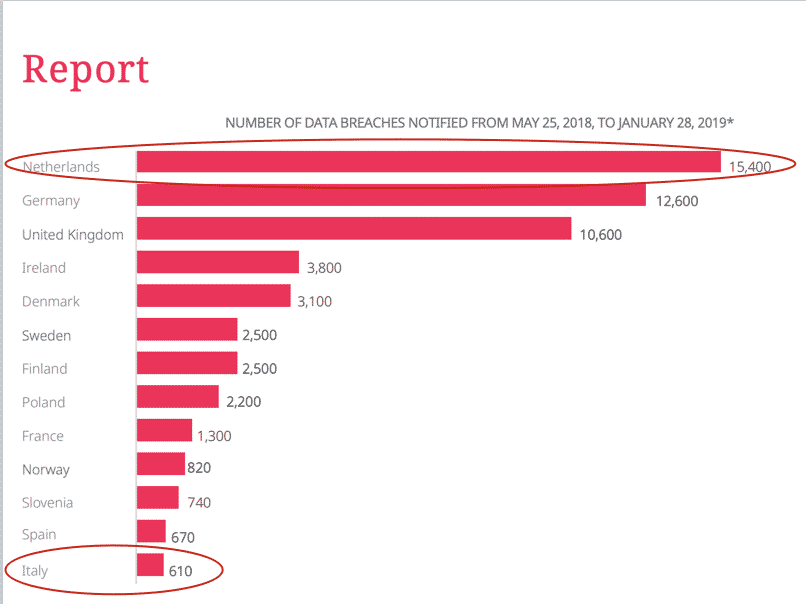
4. Figures on the number of Italian data breach notifications might hide a lack of compliance
According to a report published by DLA Piper, the number of data breach notifications performed in Italy is considerably lower than the one of other jurisdictions.
As showed in the chart, the gap between Italy and The Netherlands, Germany and the UK is extremely broad. The possible reasons of the gap might be that in some countries there is a tendency to notify any possible data breach since companies are worried about fines and want to delegate to the local data protection authority the assessment which would be in breach of the principle of self-assessment that is provided by the GDPR.
But the low number of notifications in Italy can also be due to the fact that companies sometimes do not notify since
- either they are not even aware that a conduct can amount to a data breach;
- or they prefer not to notify since they hope not to be investigated.
Indeed, based on our experience, the Garante reviews data breach notifications and investigates on them. But the lack of notification of a data breach might be trigger the fines provided by the GDPR during a period when they are meant to become even more aggressive since in May 2019 it will expire the period in which the Garante will take into account the first applicability of the GDPR in calculating the applicable fines.
ACTION NEEDED: Make sure that there is a detailed internal policy on how to handle a data breach and such policy is also translated into obligations on the suppliers that shall have a dedicated channel for the notificaton of data breaches. Also, run trainings on the matter and use a tool to assess the obligation to notify/communicate data breach. For instance DLA Piper developed a tool based on the guidelines of ENISA and the Article 29 Working Party.
5. Cybersecurity is the new challenge and human error is main risk
Cybersecurity is a major threat for any business. But the circustance that over 80% of data breaches are due to human errors is less known. 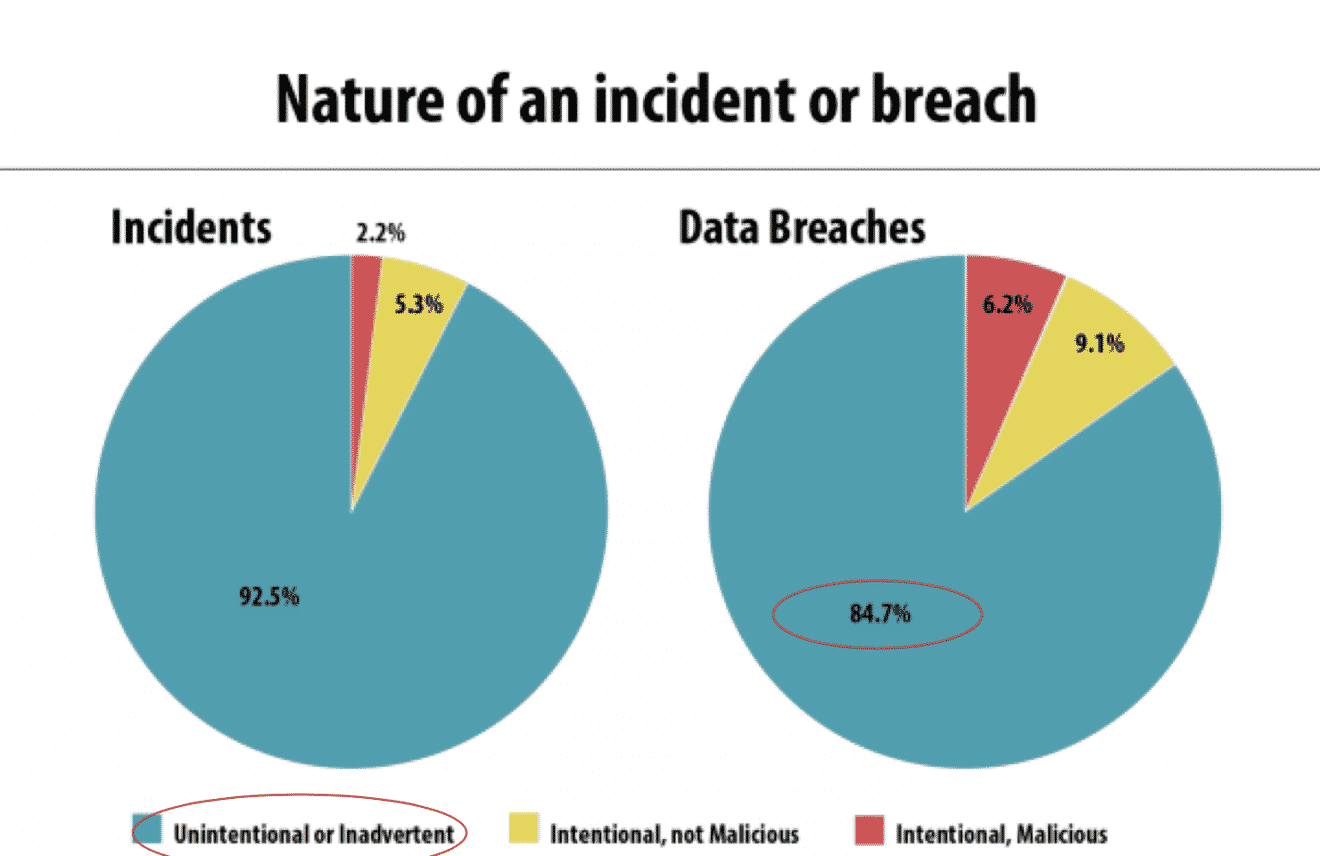
Human errors can be the source of a cyber attack since employees might plug a USB Key found on a plane in their work PC, open an email contain a virus or use always the same password for all their email account that is used for a so called “fake CEO” cyber attack.
This circumstance makes crucial to
- have appropriate measures implemented in advance to limit risks by means for instance of organizational measures, to assess consequences on contractual arrangements of the attack, to have a plan to react to the attack and have an adequate cybersecurity insurance coverage;
2. adopt effective measures to identify the cyber attack, to perform regulatory notifications, liaising with competent authorities, and to ensure business continuity, minimizing negative effects; and
3. implement actions to mitigate liabilities in potential disputes against suppliers and employees as well as competent authorities.
ACTION NEEDED: Ensure that there are both organizational and technical measures to reduce the cyber risk. No technical measure can be sufficient against human errors. Therefore employees should be trained, controlled against misbehaviours and tested.
There is no doubt that the attendees of the event came back to their office with a quite long “to-do-list“.